#browser hijacker
Explore tagged Tumblr posts
Text
youtube
If you're looking to remove Fortyfy and Surfsee extensions on Chrome, then watch this video for a step-by-step guide on how to do it. Keep your browser clean and running smoothly with these easy tips!
#how to remove extensions in google chrome#how to remove fortyfy and surfsee extensions on chrome#how to remove extension in google chrome#how to remove fortify extension#how to remove surfsee extensions#how to remove extensions from google chrome#remove extensions chrome#remove extensions google chrome#how to uninstall chrome extensions#search hijacker#anti-malware#browser hijacker#fortyfy#malware#surfsee#delete extension from chrome#how to remove google extensions#Youtube
0 notes
Text
how does neopets STILL have that browser hijacker ad embedded into the classic arcade page? is the arcade the only page it’s still on? that thing’s been there for, what, 2 years? 3? 5? no less than 3. i don’t even know, long enough that i forgot about it. it got far enough past ublock that my antivirus had to smack its hands instead.
#yes neopets has had a browser hijacker in one of its pages for 3 years. they just let that happen.#it’s the exact same one#admittedly it used to turn up on more pages but now it only seems to be left on this one. i do not know why or HOW it wasn’t removed fully#neopets#switch speaks
9 notes
·
View notes
Text
if you have the Honey browser extension installed, uninstall it immediately. big big story broke on youtube today strongly indicating that Honey has been massively defrauding basically everyone who does any business with them at every level, including influencers, customers, and actual retailers.
the short version of ONE of the alleged crimes is that they've been hijacking referral links and codes. if you have honey installed on your browser at all, and you use any referral code from anyone, there is a high probability honey will swap out the referral link identifier for their own even if they don't provide a coupon at checkout.
they also are just lying to you, and hiding coupons that very much exist. they're completely fraudulent
paypal bought honey in 2019 for 4 billion, so paypal has been strip mining the influencer economy for 5 years now. the amount of money that's been essentially stolen is unfathomable
43K notes
·
View notes
Text
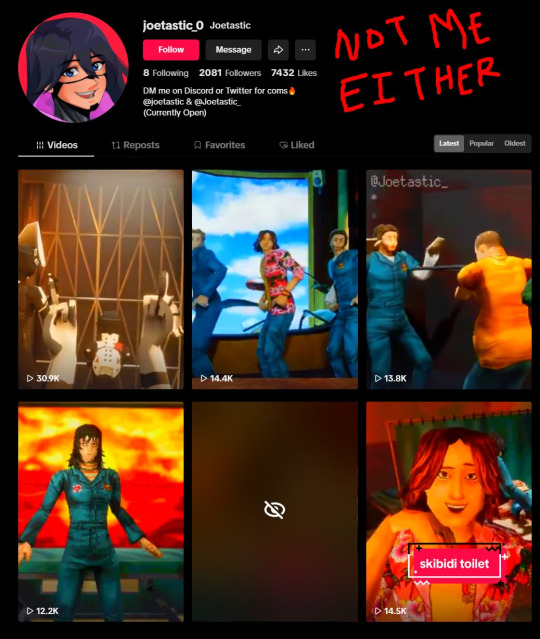
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
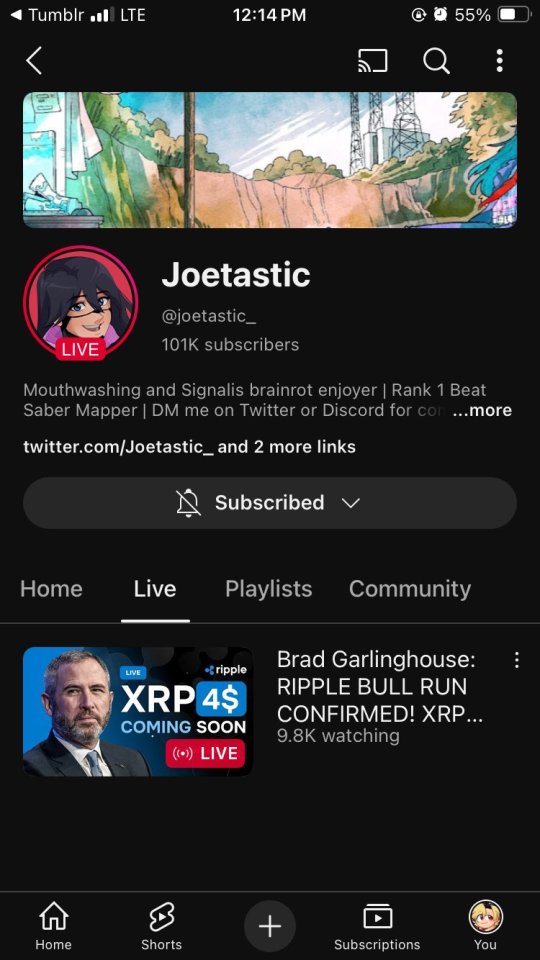
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
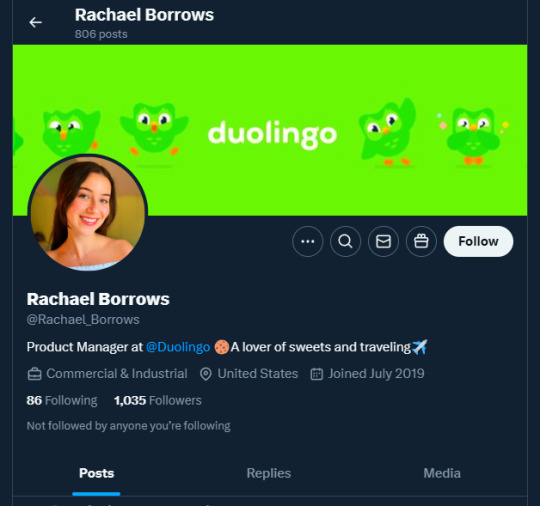
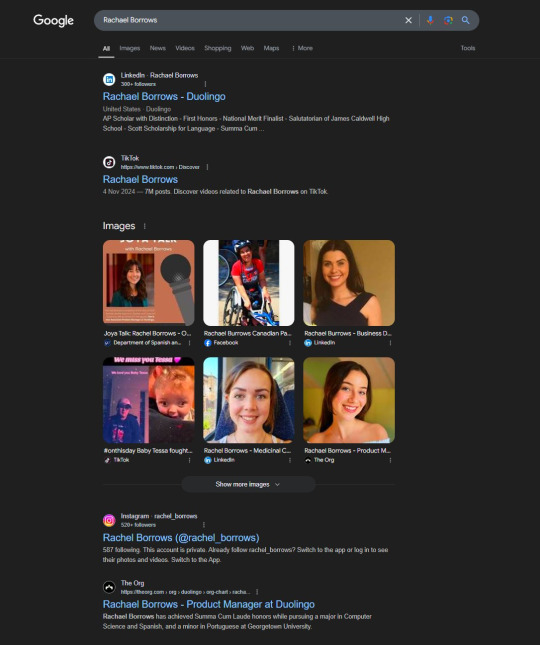
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
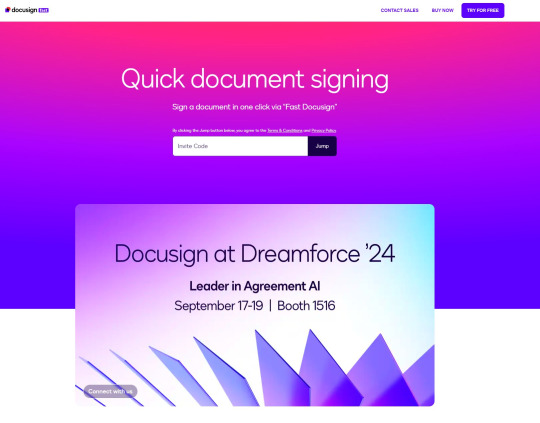
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
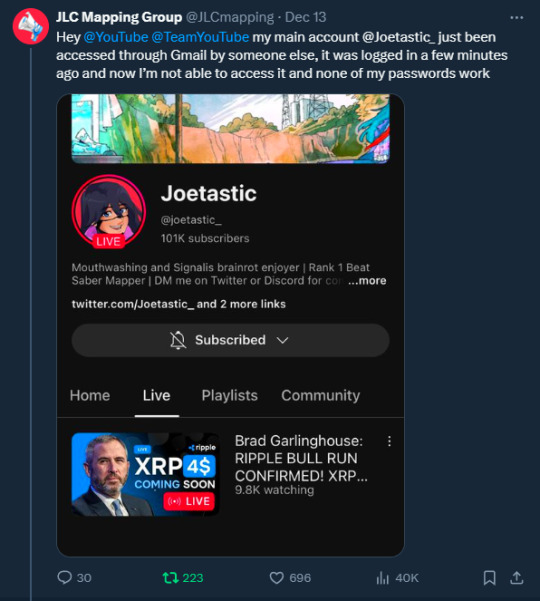
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
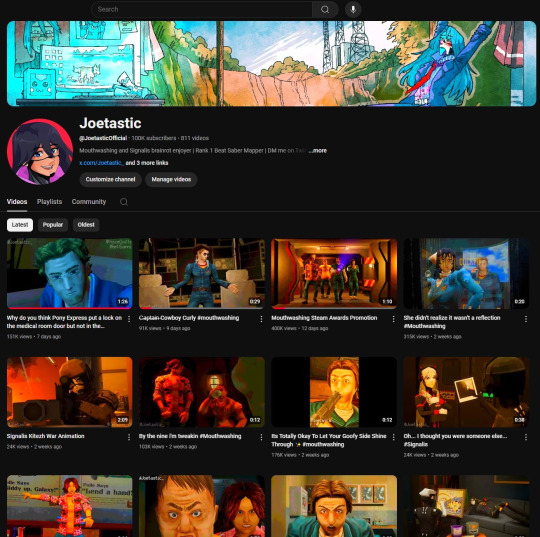
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
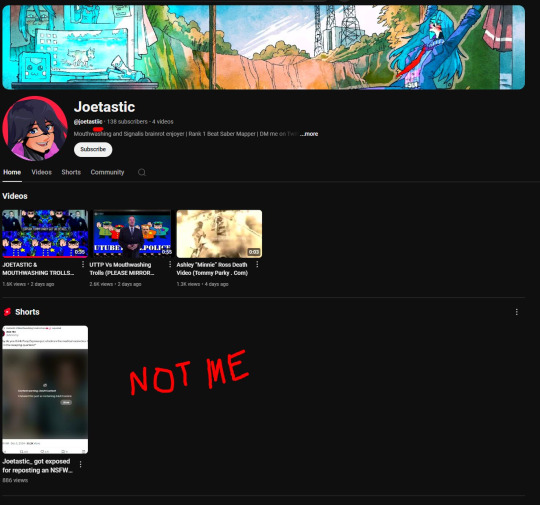
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
How to Spot Instagram Social Engineering Scams

View On WordPress
#Bot detection#Bots#Bots to inflate numbers#Browser hijackers#Clicks#Command and control server#Concert scams#Contest scams#Contests#Copyrights#Cyber awareness#Cyber safety tips#Cyber threats#Cybercrime#Cybersecurity#Cybersecurity best practices#Cybersecurity education#demographics#Digital threats#Direct email#Domain name verification#Domain names#Events#Fake accounts#Fake giveaways#Fake profiles#Fake publishing agents#followers#Fraudulent schemes#Impersonation prevention
1 note
·
View note
Text
GUYS WHATS THAT ONE POST ABOUT GETTING RID OF SHIT WITH UBLOCK
I had to restart shit from my browser and its extentions sooooooooooo
#hhghlkjasbhdkjasdghkjhasdgjk#my pc resetting did NOTHING good for me#it just made me realize i hade a browser hijacker#please
0 notes
Text
One thing I noticed talking about Linux and free software is that a lot of people seem afraid of learning things about technology. I constantly read things like "I hate windows, but switching to linux would mean learning a new OS, and you have to be some super-smart programmer-hacker to do that." Or even: "Switching to firefox would mean switching browsers and I don't know how"
And that is precisely the attitude tech companies like Microsoft and Apple try to instill in their users in order to control them. They create these simple and “friendly” user interfaces for their products, but these hide information. From their OS being pre-installed to their settings apps, they keep people from learning things about how their computer works, and letting the companies make the decisions for their users.
I think people are underestimating themselves and overestimating how hard it is to learn new things are. It is like Windows/Macos have taught them some kind of technological learned helplessness. Not knowing how computers work and being afraid to learn how is how companies like Microsoft controls you, and justifies that control.
For example, people hate the forced and automatic system updates on Windows. And Microsoft justifies it as necessary because some people don’t know that their computer needs security updates and therefore don’t update, so they have to force the updates on them. That’s definitely true, and Microsoft’s tech support people is definitely very aware of that but it is a operating system that presumes that the user is incompetent and therefore shouldn’t control their own computer. And of course Microsoft abuses that power to force privacy-invading features on their users. Windows updates are also badly designed in comparison, no Linux distro I’ve used required the update program to hijack the entire computer, preventing the user from doing other things, but Windows does.
This is the dark side of “user-friendly” design. By requiring zero knowledge and zero responsibility for the user, they also take control away from the user. User-friendly graphical user interfaces (GUI) can also hide the inner workings of a system in comparison to the command line, which enables more precise control of your computer and give you more knowledge about what it is doing.
Even GUIs are not all made equal in regards to this, as the comparison between the Windows Control panel and their newer Settings app demonstrates. As I complained about before, Windows have hidden away the powerful, but complex Control Panel in favor of the slicker-looking but simplified and less powerful Settings app for over a decade now.
Of course this is a sliding scale, and there is a sensible middle-ground between using the command line for everything and user-friendly design masking taking control away from the end user.
There are Linux distros like Linux Mint and MX Linux who have created their own GUI apps for tasks that would otherwise use the command line, without taking control away from the user. This is mainly because they are open source non-profit community-driven distros, instead of being proprietary OSes made by profit-driven megacorps.
Still, giving that control to the user presumes some knowledge and responsibility on part of the user. To return to the update example, by default both Mint and MX will search and notify you of available updates, but you will have to take the decision to download and install them. Automatic updates are available in both cases, but it’s opt-in, you have to enable that option yourself. And that approach presumes that you know that you should update your system to plug security holes, something not all people do. It gives you control because it presumes you have knowledge and can take responsibility for those decisions.
All this also applies to the underlying fact that practically all pre-built computers nowadays have an operating system pre-installed. Few people install an OS themselves nowadays, instead they use whatever came with the computer. It’s usually either Windows or MacOS for desktops/laptops, and Android/IOS for smartphones (which are also a type of computer).
Now all this is very convenient and user-friendly, since it means you don’t have to learn how to install your own operating system. The OEM takes care of that for you. But again, this is a convenience that takes choice away from you. If you don’t learn how to install your own OS, you are stuck with whatever that is on the computer you bought. It’s probably precisely this step that scares people away from Linux, few people have installed even Windows, and installing your own OS seems impossibly scary. But again, learning is the only way to take back control. If you learn how to install an OS off an USB stick, you now have choices in what OS to use. (Sidenote: the hard part IMO is not the actual install process, but fiddling with the BIOS so it will actually boot from the distro on the USB stick. This old comic strip illustrates this very well).
That’s how life is in general, not just computers. Having control over your life means making decisions based on your own judgment. And to make sensible, rational decisions, you have to learn things, acquire knowledge.
The only other alternative is letting others take those decisions for you. You don’t have to learn anything, but you have no control. And in the tech world, that means big corporations like Microsoft, Google and Apple will make those decisions, and they are motivated by their own profits, not your well-being.
Computers have only become more and more capable and more important in our lives, and that can enable wonderful things. But it also means more power to the tech companies, more power over our lives. And the only way to resist that is to learn about computers, to enable us to make our own decisions about how we use technology.
902 notes
·
View notes
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
453 notes
·
View notes
Text
So I just discovered that Reddit broke the "open image in new tab" button. If you go to a reddit page with an image (I happened to be looking at this one but I don't think it matters), and you click "open image in new tab" you get sent to a reddit page displaying the image, rather than just opening the image file in a new tab.
And first of all, obviously I'm offended and this is a terrible change that they shouldn't have done. It's awful.
But the thing I'm confused about is how it works mechanically. Like, isn't the whole point of the "open image in new tab" button that it takes the image file that is being displayed, and opens that file in a new tab? That seems like it should be entirely browser-side, in which case it shouldn't be hijackable in that way.
What are they actually doing to implement that?
(You can still right-click save the image, and then open that in a new tab, and that works perfectly normally.)
230 notes
·
View notes
Text
I've been researching and experimenting around rehabilitating my relationship with technology for a few years now. What I've realized is there's a big gap between what the research shows and what gets bumped by algorithms like YouTube - which is probably not an accident given the aims of the algorithm.
Here are my biggest takeaways so far:
- Dumbphones, lockboxes, switching to physical media, most everything you see online about coping with tech overwhelm - these plus a very long drying out period are best in cases of genuine tech addiction. Otherwise it's overconsuming to solve and overconsumption problem. Our attempts to rehabilitate our relationships with tech are being hijacked and comodified which keeps us dissatisfied/on the hamster wheel.
- Not all screen time is created equal - research shows this. Some impacts people positively, some neutrally, some negatively. Targeting screen time as a metric tends to make people feel happier in the short term by minimizing the negative category but this often leads to a level of untenable friction toward the positive and neutral types in the long term that tends to lead to a relapse and "binging" the negative. Shame leads to a repeat of the cycle.
- Social media is consistently shown as one of the most negative impacts on psychological wellbeing. Your biggest bang for your buck will be in either leaving, modifying, or heavily structuring your use of social media.
- If you can't leave social media, taking it off of your phone and using a plug in to block the feed + ads on desktop can help. Still want to see what your friends and family are posting? Create a folder for bookmarks of direct links to their profile/main pages or use an RSS reader like Feedly. Curate it carefully; avoid outrage regardless of whether you share it's leanings.
- There are other targets that I personally think would make people happier with their tech usage overall: eliminating/minimizing subscriptions, avoiding ads, prioritizing privacy, and using human curation. While they each have benefits on their face, the shifts in usage they encourage are ones that people generally report more satisfaction with.
- Eliminating/minimizing subscriptions means more money each month but it also usually means cutting out things like streaming. The big non-financial con of streaming is that it can lead to overwhelm and perfectionism - thereby decreasing satisfaction. The upside of cutting it out is that it pushes people toward renting, owning, or ripping media they love which requires intentionality and curation.
- If really you want free streaming, check out whether your library has Kanopy, Hoopla, or Freegal. You can still get some of the benefits by embracing the reduced selection they offer. They also likely still have CDs and DVDs you can rip for your personal collection.
- Avoiding ads and prioritizing privacy go hand in hand. This usually means using an ad blocker and shifting away from Apple and Google and Meta where possible - deleting apps, switching services, blocking feeds, switching browsers. I can't deGoogle completely at the moment but when I shifted in the ways I was able, I started scoring my time online more positively and I took more breaks/spent less time on it.
- Seek out human curation: library newsletters, listen to local radio, ask your friends and family, check out round ups and newsletters from your favorite creators, share your own. Human curation is less likely to be driven by business interests and while there's no algorithm free media rec these days, they're not being given to trap you on a platform.
- Focusing on a quantitative metric (like screen time) is the gateway to consumerism. Stop looking for a cure and start discovering your personal philosophy. Talking about the algorithmic alienation from our actual feelings and desires is too much for this post but simply put there is no "pure" experience you're missing out on by using a screen. Notice how you're feeling, respond with kindness, and let the rest go. Shame is a weapon in the hands of corporations.
Hope this is helpful for someone out there.
68 notes
·
View notes
Text
youtube
If you're looking to remove Fortyfy and Surfsee extensions on Chrome, then watch this video for a step-by-step guide on how to do it. Keep your browser clean and running smoothly with these easy tips!
#how to remove extensions in google chrome#how to remove fortyfy and surfsee extensions on chrome#how to remove extension in google chrome#how to remove fortify extension#how to remove surfsee extensions#how to remove extensions from google chrome#remove extensions chrome#remove extensions google chrome#how to uninstall chrome extensions#search hijacker#anti-malware#browser hijacker#fortyfy#malware#surfsee#delete extension from chrome#how to remove google extensions#Youtube
0 notes
Text
Search for google using Windows' Edge browser and instead of sending you to actual google.com, Microsoft now hijacks your search and sends you to a Bing search screen that looks suspiciously like google.
And before anyone 'helpfully' suggests we all stop using Windows, please remember that many people are forced into the experience via work or family. Not everyone has direct control of their electronic devices.
71 notes
·
View notes
Text
Did You Download This Steam Game? Sorry, It's Windows Malware | PCMag
40 notes
·
View notes
Text
📢 “Did YOU decide to read this? Or did your meat suit trick you into thinking that?”
🧠 You’re not the main character. You’re a split-brained, snack-chasing biological sock puppet who believes in "toxic" masculinity, sorry not sorry.

🧬 Welcome to the Existential Meat Grinder: Where Free Will Goes to Die
Let’s get one thing straight right out the gate:
You didn’t “decide” to read this.
Your body did.
Your eyes flicked over it, your dopamine fired, and now your fragile little narrative ego is scrambling to justify it like you made a “choice.”
🛑 You didn’t.
Your brain made that move before you even showed up to the party.
And don’t take that personally — you're just one of 8 billion hairless apes walking around pretending your decisions are handcrafted by logic and intention, when really?
You’re basically a moist Roomba with unresolved trauma.
🧠 Split Brain, Split Personality, Split Reality
Ever heard of split-brain syndrome? No? Sit down.
In experiments where the connection between the brain’s hemispheres (the corpus callosum) was surgically severed — for epilepsy patients — each half of the brain literally started doing its own thing.
👁 Left hand does one task.
🧠 Right brain controls it.
🧠 Left brain has no clue why and makes up a reason.
Let that marinate:
Your brain would rather LIE than admit it doesn’t know why it’s doing something.
You’re out here defending your “decisions” like a philosophical gladiator, and meanwhile your neurons are freelancing with no manager.
You are not the CEO of your brain.
You're the PR department — desperately spinning random sh*t into a cohesive story that helps you sleep at night.
🥴 That Snack? Yeah, You Didn’t Choose That Either
Let’s talk about your little late-night fridge crawl.
You thought, “I deserve a snack.”
Nah. Your gut bacteria sent up a chemical missile that hijacked your consciousness and said:
“Move meat stick toward cheese or I start the spiral.”
That wasn’t self-care. That was bacteria blackmail with a glucose ransom.
You didn’t “choose.” You rationalized.
And you did it after your body had already opened the fridge and committed the crime.
🎯 Thought → Feeling → Action?
Wrong.
🤡 More like:
Action.
Confused justification.
Tweet about “intuitive eating.”
🎮 Free Will Is Just a Loading Screen
You think you're in control?
That you are the one making your choices?
Sweetheart, your decisions are pop-up ads in a browser you don’t own.
The illusion of control is so damn good it’s got you defending it with your whole chest.
But neuroscience isn’t even subtle about it anymore.
Decisions? Traced back to brain activity that starts before you’re consciously aware of it.
By the time you “decide,” the machinery already committed.
You’re just signing the receipt and calling yourself the chef.
🧘♂️ The Delusion of “Mindfulness”
“But I meditate,” you cry.
Cool. So now you’re consciously watching your subconscious processes dominate you in real time. Congrats. You’ve upgraded from puppet to meta-puppet.
🧠 Thoughts arise.
🥴 You watch them.
👀 You label them.
🎭 And then? You think you're transcending, when really you’re just becoming aware of how little control you have.
You’re not mastering your mind.
You’re watching the train crash slower.
🤯 The Conscious Mind = PR Guy, Not CEO
You think you’re running the show.
Newsflash:
You’re not the general.
You’re the press secretary.
You show up after the decision’s made, spit out a justification, and get applauded for “being self-aware.”
“I chose to go to the gym because discipline matters.” No. Your cortisol levels spiked, your stress hormones bullied your nervous system, and your ego invented a noble reason because chaos makes you wet with anxiety.

😈 Who’s Actually Running You?
Here’s the real horror:
🧬 DNA: 3.5 billion years of evolutionary paranoia whispering: eat, mate, survive, repeat.
🦠 Gut biome: A literal crowd of bacteria screaming for snacks like a drunk mosh pit.
🧪 Hormones: Neurochemical puppeteers flipping switches based on weather, smell, and whether Chad texted back.
🧠 Brain: Firing off responses to stimuli like a squirrel with a caffeine addiction.
And you?
You think you’re “choosing.”
Sweetheart, you’re barely steering.
🪞 Still Think You’re Special?
You didn’t pick your genes.
You didn’t choose your trauma.
You didn’t design your brain.
You didn’t install your habits.
And yet you strut around like Captain Executive Function.
You are the sum of inputs + a meat processor + a story you keep rewriting to make it look intentional.
🧠 You don’t make decisions.
You narrate them.
You defend them.
You lie to yourself about them.
And THEN you post about it on Instagram like you’re a life coach.
🧻 Existential Crisis Starter Pack:
“Was that me… or my gut microbiome?”
“Did I want that coffee or did my dopamine?”
“Is love real or just a serotonin drip with a playlist?”
“Am I making a choice, or am I the illusion of a choice built out of reactions?”
😅 Welcome to the jungle, baby.
It’s neurons all the way down.
🧠 TL;DR:
You didn’t decide to read this.
Your brain tricked you into justifying it afterward.
You’re a walking feedback loop in a trench coat.
Free will? Cute concept. Trash execution.
Your gut bacteria have more influence over your life than your conscious mind.
And the meat suit is laughing.
⚖️⚖️⚖️
LEGAL DISCLAIMER:
This post is legally protected under freedom of speech and expressive commentary. Any psychological damage, existential dread, or sudden urge to argue in the comments is your responsibility, not mine.
This is not medical advice. This is philosophical pest control.
⚖️ Offense ≠ harm.
⚖️ Confusion ≠ contradiction.
⚖️ You = 86% biochemical instinct + 14% bad coping mechanisms.
Welcome to the truth. It doesn’t care if you’re offended.
⚖️⚖️⚖️
📢 Read this again if your ego's still breathing.
🧠 Share it with the next person who says “I’m just listening to my body.”
📩 DM it to that friend who thinks their Fitbit decisions = free will.
💬 Drop a comment if your gut bacteria are currently demanding cheese.
🔥 Repost if you’ve ever caught your brain making sh*t up mid-justification.
💀 Save this for the next time you think you’re the main character.
👑 Spoiler: You’re not. Your serotonin is.
#twitter#twitter memes#tweets#hauntedmeatsuit#us politics#dank memes#humor#meme#writing community#writing prompt#writers on tumblr#funny post#jokes#news#life#life lessons#feminism#funny memes#tumblr memes
27 notes
·
View notes
Text

NEOPETS YOU HAVE HAD A BROWSER HIJACKER EMBEDDED IN YOUR FUCKING CLASSIC GAME ARCADE WEBSITE FOR THE PAST ~5 YEARS ARE YOU OUT OF YOUR GENUINE MINDS
#BRO WAKE UP IT'S 2006#WELCOME BACK ADVER-VIDEO#THIS WOULD BE FUNNY IF IT WASN'T FOR THAT#switch speaks#neopets
27 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes